Cryptojacking - Cryptomining in the browser — ENISA
Por um escritor misterioso
Last updated 20 maio 2024

The technique of hijacking browsers for mining cryptocurrency (without user consent) is called

Cryptojacking - Cryptomining in the browser — ENISA

Rundown of the Top 15 Cybersecurity Threats of 2019-2020 — Long Law
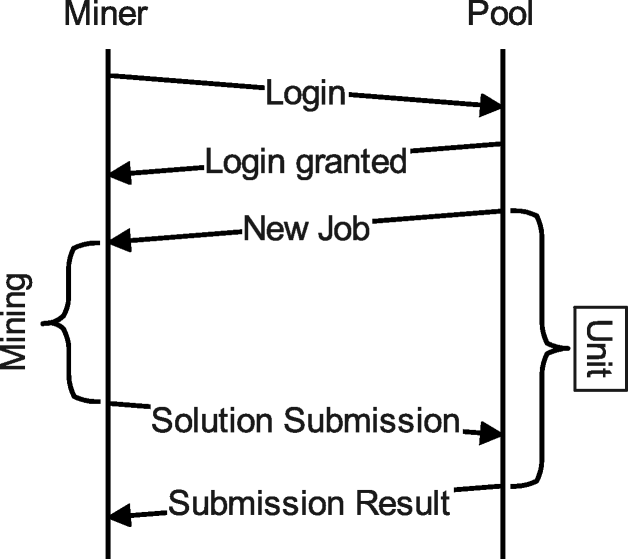
Detection of illicit cryptomining using network metadata

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

WP2018 O.1.2.1 - ENISA Threat Landscape 2018 PDF, PDF

Threats - understanding Cyber Attacks
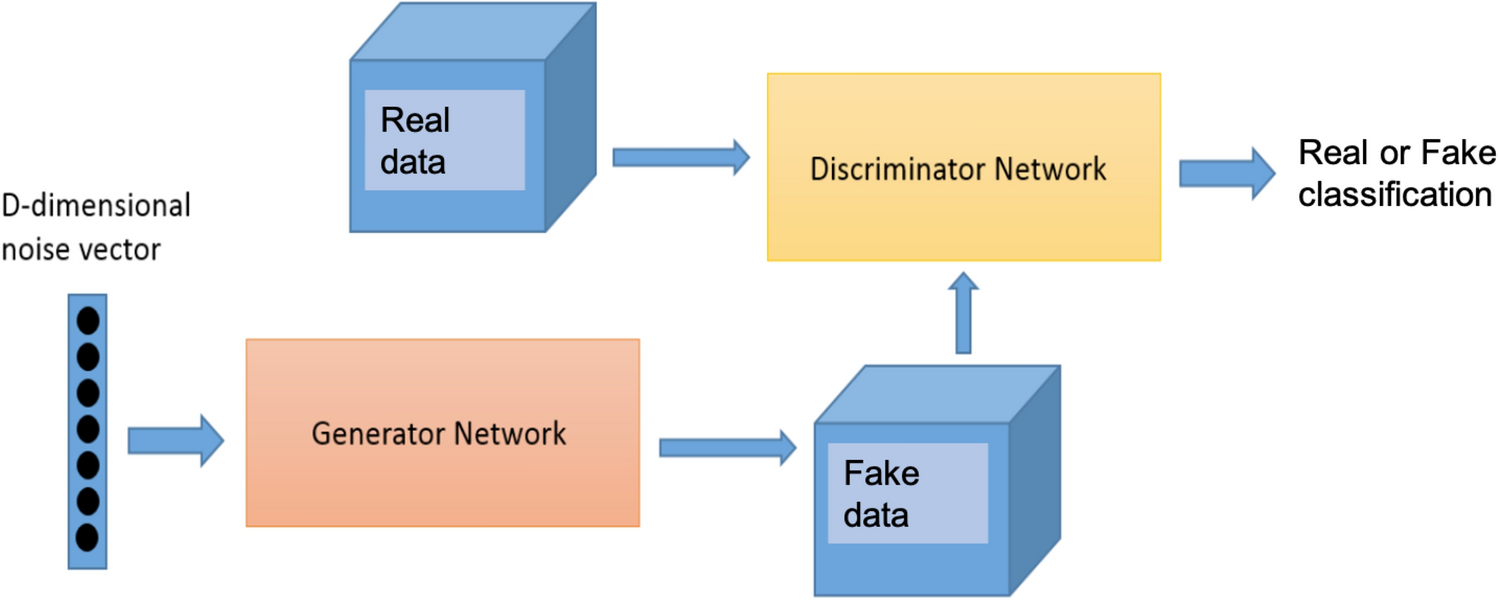
Synthetic flow-based cryptomining attack generation through

Reinforcing Financial Cybersecurity in the Eurozone by The

What is Cryptojacking. Criminals are now using ransomware-like

Cryptojacking: Has Your Computer Been Hijacked Yet? - Kratikal Blogs

What You Must Know About Cryptojacking in 2022
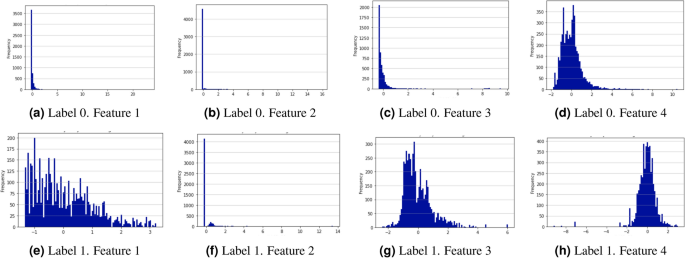
Synthetic flow-based cryptomining attack generation through
Recomendado para você
-
minerBlock20 maio 2024
-
 minerBlock - Download & Review20 maio 2024
minerBlock - Download & Review20 maio 2024 -
 Fake Ad Blocker Delivers Hybrid Cryptominer/Ransomware Infection20 maio 2024
Fake Ad Blocker Delivers Hybrid Cryptominer/Ransomware Infection20 maio 2024 -
 My Early Bitcoin ASIC Miners (2013-2014) - Pictures / History20 maio 2024
My Early Bitcoin ASIC Miners (2013-2014) - Pictures / History20 maio 2024 -
Yes! Hackers are using your computer to make money (Crypto Currency).20 maio 2024
-
 12 Air Date 01/16/1960 Stock Photos, High-Res Pictures, and Images - Getty Images20 maio 2024
12 Air Date 01/16/1960 Stock Photos, High-Res Pictures, and Images - Getty Images20 maio 2024 -
 How to Eat Like a 19th Century Colorado Gold-Miner - Gastro Obscura20 maio 2024
How to Eat Like a 19th Century Colorado Gold-Miner - Gastro Obscura20 maio 2024 -
 AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock20 maio 2024
AdBlocker for Safari ▻ AdBlock by Content blocker & Website Adblocker. Ad block remove ads - safe internet browsing. Adblock20 maio 2024 -
 Men's Basketball - UTEP Miners20 maio 2024
Men's Basketball - UTEP Miners20 maio 2024 -
 Colorado Avalanche Game Used Pro Stock Bauer Mach Glove and Blocker Miner #120 maio 2024
Colorado Avalanche Game Used Pro Stock Bauer Mach Glove and Blocker Miner #120 maio 2024
você pode gostar
-
Rino on X: Spider-Man 2 is shaping up to be a GOTY contender20 maio 2024
-
What is the meaning of Lolz? - Question about English (US)20 maio 2024
-
Steam Workshop::FNaF World: FNaF 4 (MODEL LINK IN DESC)20 maio 2024
-
Jogo War Júnior | Jogo de Tabuleiro Grow Usado 83813320 | enjoei20 maio 2024
-
 Roblox Best Horror Games To Play20 maio 2024
Roblox Best Horror Games To Play20 maio 2024 -
 Turbofil Pré Filtro de ar de Turbina, Compacto, Alta Eficiência20 maio 2024
Turbofil Pré Filtro de ar de Turbina, Compacto, Alta Eficiência20 maio 2024 -
 Best College Campuses20 maio 2024
Best College Campuses20 maio 2024 -
 Camiseta Oakley Ellipse Tee20 maio 2024
Camiseta Oakley Ellipse Tee20 maio 2024 -
Atlanta vs Quilmes Atlético Club live score, H2H and lineups20 maio 2024
-
 The Vampire Diaries 6x22: I'm Thinking of You All the While20 maio 2024
The Vampire Diaries 6x22: I'm Thinking of You All the While20 maio 2024



