Initial access broker repurposing techniques in targeted attacks
Por um escritor misterioso
Last updated 14 maio 2024

Describing activities of a crime group attacking Ukraine.

Initial access broker repurposing techniques in targeted attacks against Ukraine

So long and thanks for all the 0day, NCC Group Research Blog
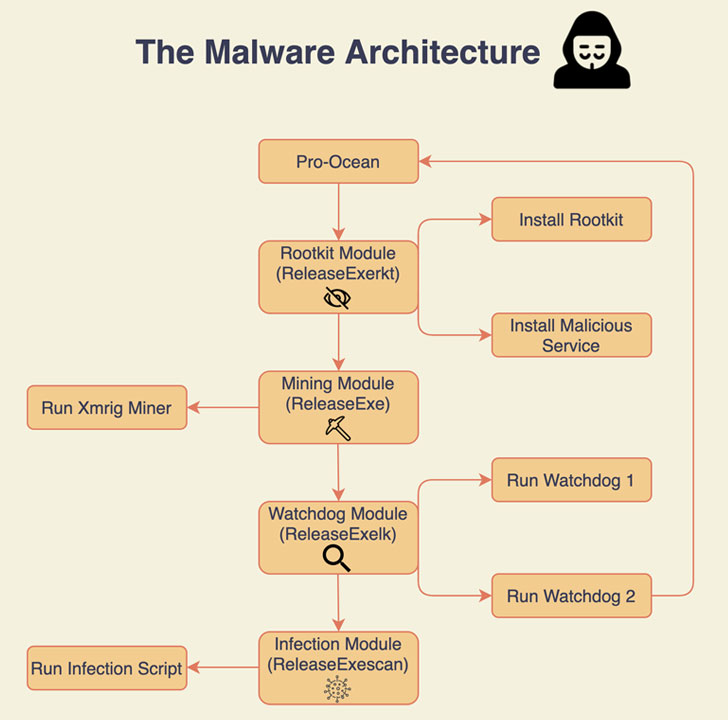
New Cryptojacking Malware Targeting Apache, Oracle, Redis Se - vulnerability database

Blogs Dell Technologies Info Hub

Scraping-as-a-Service: How a Harmless Tool Became a Cyber Threat

Security in product lifecycle of IoT devices: A survey - ScienceDirect

Google: Former Conti ransomware members attacking Ukraine
GitHub - CyberMonitor/APT_CyberCriminal_Campagin_Collections: APT & CyberCriminal Campaign Collection

A survey on recent optimal techniques for securing unmanned aerial vehicles applications - Syed - 2021 - Transactions on Emerging Telecommunications Technologies - Wiley Online Library
6 Types of Database Hacks Use to Obtain Unauthorized Access

Former Conti Ransomware Members Join Initial Access Broker Group Targeting Ukraine

Google Says Former Conti Ransomware Members Now Attack Ukraine - Privacy Ninja

Cisco Umbrella discovers evolving cyberthreats in first half of 2020

Security in product lifecycle of IoT devices: A survey - ScienceDirect

Initial Access Brokers How They're Changing Cybercrime
Recomendado para você
-
 Analysis Group - Crunchbase Company Profile & Funding14 maio 2024
Analysis Group - Crunchbase Company Profile & Funding14 maio 2024 -
 Careers - Analysis Group14 maio 2024
Careers - Analysis Group14 maio 2024 -
 Working at Analysis Group14 maio 2024
Working at Analysis Group14 maio 2024 -
 Analyst - Analysis Group14 maio 2024
Analyst - Analysis Group14 maio 2024 -
 Prigozhin interests and Russian information operations14 maio 2024
Prigozhin interests and Russian information operations14 maio 2024 -
 GAR 100 - 13th Edition - Global Arbitration Review14 maio 2024
GAR 100 - 13th Edition - Global Arbitration Review14 maio 2024 -
 2022 Golden State Institute - California Lawyers Association14 maio 2024
2022 Golden State Institute - California Lawyers Association14 maio 2024 -
 Job Listings at Analysis Group, Inc.14 maio 2024
Job Listings at Analysis Group, Inc.14 maio 2024 -
 Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts14 maio 2024
Hydraulic Analysis Limited Surge Analysis & Flow Assurance Experts14 maio 2024 -
 USC/AG Antitrust and Competition Event14 maio 2024
USC/AG Antitrust and Competition Event14 maio 2024
você pode gostar
-
 Pixilart - Stickman T Pose by FireTiger14 maio 2024
Pixilart - Stickman T Pose by FireTiger14 maio 2024 -
 Marvel Figuras de Cinema - Thor (De: Thor Ragnarok) - Edição 0414 maio 2024
Marvel Figuras de Cinema - Thor (De: Thor Ragnarok) - Edição 0414 maio 2024 -
 gta 6 leaked gameplay (WOW!)14 maio 2024
gta 6 leaked gameplay (WOW!)14 maio 2024 -
 Roblox Noob, UnAnything Wiki14 maio 2024
Roblox Noob, UnAnything Wiki14 maio 2024 -
 Magic 8 Ball Retro14 maio 2024
Magic 8 Ball Retro14 maio 2024 -
 The #MadeInLCI game Bonelike wins the Best 3D Video Game Award14 maio 2024
The #MadeInLCI game Bonelike wins the Best 3D Video Game Award14 maio 2024 -
 Bichinho Virtual Tamagotchi 168 Animais Divertido14 maio 2024
Bichinho Virtual Tamagotchi 168 Animais Divertido14 maio 2024 -
 POTTERY BARN OUTLET - 10 Photos & 22 Reviews - 1770 W Main St, Riverhead, New York - Furniture Stores - Phone Number - Yelp14 maio 2024
POTTERY BARN OUTLET - 10 Photos & 22 Reviews - 1770 W Main St, Riverhead, New York - Furniture Stores - Phone Number - Yelp14 maio 2024 -
 Camisa Ícone Sports Dragon Azul - FutFanatics14 maio 2024
Camisa Ícone Sports Dragon Azul - FutFanatics14 maio 2024 -
 The Battle of the Sexes - Rotten Tomatoes14 maio 2024
The Battle of the Sexes - Rotten Tomatoes14 maio 2024